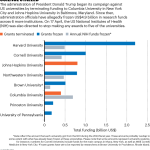
Wireless Tapping: A New Frontier in Digital Privacy Risks
In recent years, the digital world has seen a surge in innovative yet concerning surveillance methods. One particularly nerve-racking development involves “wireless tapping,” a technology that decodes laughter, whispers, and entire conversations from the subtle vibrations produced by a cell phone’s earpiece. While exciting from a technological standpoint, this technique raises a lot of questions about digital privacy, ethical use, and potential misuse. This opinion editorial digs into the research and its implications, offering viewpoints that strike a balance between innovative technology and the delicate art of protecting personal privacy.
Understanding the Wireless Tapping Technique
The most recent research coming out of Penn State University has grabbed headlines with its claim that radar sensors can capture conversation details from a phone’s vibrations—even from up to three meters away. By tapping into the tiny movements induced by sound, researchers adapted an open-access, large-scale AI speech recognition model, known as “Whisper,” to transform these vibrations into text transcriptions. Although the results are only about 60% accurate for a vocabulary reaching 10,000 words, they shed light on the potential for security breaches in our daily communication.
Radar Sensors and Their Everyday Uses
Millimeter-wave radar sensors are not a new concept. They have been used for many years in self-driving cars, motion detectors, and even in boosting 5G wireless networks. However, the twist here is that these sensors were repurposed to detect the confused bits of swaying vibrations from cell phone earpieces and then processed via AI algorithms. It’s a perfect blend of state-of-the-art hardware and modern artificial intelligence adapting to a seldom-discussed aspect of personal communication.
How It Works: The Technical Journey
The journey begins with a radar sensor picking up the subtle vibrations of a phone when someone speaks. Despite the sensor being placed only a few feet away, the movement it detects is incredibly delicate. Researchers then feed this data into a modified version of Whisper. However, Whisper was originally designed to deal with clear, everyday speech, not the noisy data derived from such a sensor. To address these tricky parts, the team employed a process called low-rank adaptation. This method retrains only about 1% of the model’s parameters to account for the messy, radar-sourced noise.
Key Steps in the Process
- Detection: Millimeter-wave radar sensors record minute vibrations from an active phone.
- Data Transmission: The collected signals are converted into digital data that carry subtle vibrations.
- Model Adaptation: An adapted version of the Whisper AI model is deployed to interpret and transcribe the noisy data.
- Final Output: The result is a rough transcription with about 60% accuracy, highlighting keywords and partial phrases.
Privacy Implications: Balancing Innovation and Safety
This emerging method of obtaining speech data remotely is packed with both promise and pitfalls. On one hand, understanding these techniques could provide key insights for developing better privacy safeguards. On the other, they open up a can of worms related to unwanted surveillance. With many of us already feeling overwhelmed about our digital lives, this new development adds another layer of tension, moving digital privacy from the realm of paranoid science fiction into something that is very much real.
Risks Posed by Remote Speech Recognition
The idea of having one’s phone – the central device for both personal and professional communications – susceptible to remote tapping is indeed intimidating. Imagine a scenario where an unauthorized actor employs this technology to capture sensitive financial or health-related conversations. While current transcription accuracy hovers around 60%, even piecing together key phrases could be enough for nefarious purposes. With keywords signaling potentially sensitive topics, the method offers a backdoor that could be taken advantage of by those with malicious intent.
The Need for Public Awareness
It is super important for the public to get into the subject of digital privacy early on. While the research is, at this point, experimental, the conversation around it provides an opportunity to educate users about potential risks in their everyday communications. By highlighting the possibility of even partial eavesdropping, society has a chance to begin working through policies that can shield personal data from unintended surveillance.
AI and Speech Recognition: Adapting Models for Noisy Data
One of the most interesting aspects of the research is how AI is being adapted to recognize speech from environments that are anything but pristine. Whisper, an open-source speech recognition model, has been leveraged for this purpose. However, as it originally catered to clean, everyday speech, researchers had to adjust its parameters to suit the challenging data coming from radar sensors.
Low-Rank Adaptation: Tweaking AI for Tough Tasks
Low-rank adaptation is a clever fix to a very tricky part of the challenge. Instead of retraining the entire model from scratch—which would be incredibly resource-intensive—the team chose to retrain only about 1% of the model’s parameters. This adaptation has allowed the already powerful model to make sense of the noisy, distorted signals captured by radar sensors. By doing so, they managed to improve transcription accuracy and provide transcriptions that, although imperfect, can still offer valuable insights in security contexts.
Comparing Remote Speech Recognition to Lip-Reading
Interestingly, researchers compared their work to the art of lip-reading. Lip readers typically capture about 30% to 40% of spoken words, yet with context clues and strong intuition, they manage to form a coherent understanding of the conversation. Similarly, the hybrid system combining radar-derived data and AI inference might only capture partial speech, but when programmed to incorporate contextual information, these partial transcriptions can become valuable. This comparison opens a new dialogue on how low-quality data might still be valuable in specific applications, such as surveillance or even law enforcement.
Privacy vs. Progress: Ethical and Policy Considerations
As we take a closer look at the research, it is essential to ask: Where does one draw the line between innovation and privacy infringement? While technologies like these offer amazing potential in fields such as security research and troubleshooting technical systems, they are also loaded with potential for abuse. When sensitive conversations can be partially transcribed from a few feet away, individuals might unknowingly sacrifice their privacy.
Ethical Dilemmas in Surveillance Technologies
Modern surveillance methods have always walked a fine line between improving security and invading privacy. With wireless tapping technology, that line becomes even more blurred. The technology itself has promising applications in detecting and preventing criminal activity. However, it is equally plausible that the same system could be adopted by bad actors looking to eavesdrop on private communications. This tense situation calls for clear ethical guidelines and substantial policy interventions.
Policy Recommendations for Protecting Digital Privacy
Given the rapid developments in such surveillance technologies, policymakers need to ensure that legal frameworks catch up with technological advancements. Some critical steps include:
- Implementing Robust Data Security Laws: Legislative action should focus on making unauthorized access to communications a clearly defined offense with significant penalties.
- Encouraging Transparency and Accountability: Companies producing advanced sensors and AI systems must be transparent about potential uses and associated privacy risks.
- Developing Industry Standards: Standard protocols for managing and securing remote data should be adopted to minimize risks related to wireless tapping.
- Public Education Campaigns: Increasing user awareness about the risks and safe practices for personal electronic devices should be prioritized.
Technical Hurdles and Areas for Improvement
Though the current state of wireless tapping technology shows promise, it still struggles with several tricky parts. The reported 60% accuracy means that a substantial margin of error exists, and detecting context or conversation nuances remains challenging. Before such technology is adopted for any regulated use, these issues must be carefully addressed.
Challenges of Processing Noisy Data
One of the core challenges is working through the inherent noise in radar data. Unlike clear audio recordings made by conventional microphones, radar-derived signals are riddled with tension and often miss the fine details of speech. Processing this kind of noisy data requires not only sophisticated AI models but also a deep understanding of the subtle parts of human conversation. The research team acknowledges that their current model is merely a first step, and much work remains to increase accuracy.
Potential Improvements and Future Research Steps
There are several avenues to improve this technology:
- Refinement in Data Collection: Experimenting with various radar frequencies and sensor positions might yield better quality data, reducing the amount of noise and increasing transcription accuracy.
- Enhanced AI Training: Further refining low-rank adaptation techniques could allow the AI to better understand the slight differences between genuine speech and ambient vibrations.
- Context-Based Adjustments: Incorporating context-aware algorithms can help piece together partial transcriptions by predicting missing parts based on previous speech patterns and conversation context.
- Increased Collaboration between Disciplines: Bringing together experts in signal processing, artificial intelligence, and privacy law might help create a holistic improvement in the system.
Future Horizons: What Lies Ahead in Wireless Surveillance?
While the current technology is in its experimental phase, the implications for both security and privacy are super important. The ability to remotely detect and transcribe conversations from minimal vibrations opens up a world of possibilities—and challenges. As researchers continue to poke around in this field, it is crucial to focus on bolstering security measures and creating robust legal frameworks to prevent misuse.
Anticipated Technological Breakthroughs
In the next decade, several breakthroughs might emerge from the foundation laid by this research:
- Miniaturized Radar Devices: Future sensors could be small enough to blend seamlessly into everyday objects, making them more accessible—and more dangerous if misused.
- Integration with IoT Devices: As the Internet of Things expands, integrating these sensors into a networked environment could both enhance security applications and open new vectors for privacy intrusion.
- Real-Time Transcription Systems: Advancements may lead to real-time conversion of vibrations to text, supporting applications in security monitoring but also raising urgent privacy concerns.
Balancing Technological Progress with Privacy Protections
While technological progress is inevitable, managing your way through the implications of wireless tapping technology will be an ongoing challenge. It is essential that both technologists and policymakers work together to ensure that digital privacy is not lost in the race for innovation. The hope is to harness the promise of these advances while keeping the potential for abuse firmly in check.
The Role of Public and Private Sectors in Shaping the Future
Given the overlap between academia, the tech industry, and government regulation, it is clear that the responsibility for managing the safe use of innovative surveillance technologies does not lie with one group alone. Instead, a collaborative approach is needed to address the little details and subtle parts that determine the overall public impact.
Collaboration Opportunities and Shared Responsibilities
A multi-pronged approach can ensure that developments in wireless tapping do not spiral out of control:
- Academic Research: Universities and research institutions should continue to explore the potential of such technologies while also meticulously documenting risks and limitations.
- Private Sector Initiatives: Tech companies can help by developing safer, more secure systems that incorporate robust privacy features into these emerging technologies.
- Government Oversight: Regulatory bodies at both the state and federal levels need to craft policies that are agile enough to respond to rapid technological changes yet steadfast in protecting privacy rights.
- Public Dialogue: Engaging the public through debates, opinion editorials, and education campaigns can foster a more informed citizenry capable of making wise decisions about privacy and technology.
Benefits of a Unified Approach
An integrated strategy can provide several key benefits:
| Sector | Role | Potential Benefit |
|---|---|---|
| Academic | Innovative research, risk assessment | Advancement in technology with a focus on public safety |
| Private | Product development, implementation of safeguards | Creation of secure devices and applications |
| Government | Legislation, oversight enforcement | Protection of consumer rights and privacy |
| Public | Feedback, advocacy, education | Informed decision-making and increased accountability |
This table underscores the idea that every stakeholder has a unique role to play in ensuring the safe evolution of surveillance technologies.
Looking at the Tricky Parts: Real-World Applications and Concerns
The wireless-tapping research is not merely a theoretical venture. If honed, these techniques could soon find themselves in real-world applications—posing both opportunities and significant challenges. From law enforcement to counterterrorism, the method could be used to intercept illegal activities. Conversely, privacy advocates warn that such technologies could easily be exploited by criminals or even governmental overreach.
Practical Applications Where This Technology Could Shine
There are several areas where radar-based speech recognition might prove beneficial:
- Security Monitoring: Law enforcement agencies could use the technology to detect and interpret suspicious communications where traditional audio surveillance fails.
- Emergency Response: In disaster scenarios, where conventional communication lines break down, remote monitoring of verbal cues could help assess situations in real time.
- Counter-Surveillance Measures: Companies and governments could also use the method to detect unauthorized surveillance devices in sensitive areas.
- Assistive Technology: For individuals with hearing impairments, a refined version of the technology might one day offer enhanced speech-to-text assistance in noisy environments.
Concerns and the Risk of Misuse
Despite these promising applications, the technology is replete with areas that are full of problems. It is nerve-racking to think that the very same method can be misused to compromise personal communications. Issues include:
- Privacy Invasion: Unauthorized tapping into personal conversations can lead to misuse of information for fraudulent or malicious activities.
- Data Security: The storage and processing of such sensitive transcriptions pose risks regarding data breaches.
- Legal Gray Areas: Existing laws may not fully cover the nuances of such advanced surveillance, leaving loopholes that can be exploited.
- Ethical Dilemmas: Balancing the benefits of improved security against the rights to personal privacy remains one of the most complicated pieces of digital ethics today.
Addressing the Challenges: A Call for Responsible Innovation
In light of these developments, it is essential to figure a path that fosters innovation while safeguarding the interests of citizens. Researchers are already taking steps to ensure that their work is used for the public good. By demonstrating the vulnerabilities inherent in current technologies, they are sparking necessary conversations about digital privacy and security measures. Establishing guidelines now could help prevent the exploitation of these emerging capabilities in the future.
Best Practices for Minimizing Risks
To protect privacy without stifling innovation, several best practices should be considered:
- Transparency in Research: Researchers must openly share their methods and findings, allowing oversight and independent verification of their results.
- Creating Secure Data Pipelines: Both the collection and storage of data must be secured to prevent unauthorized access or breaches—a tweak that might be key in protecting users’ privacy.
- Regular Reviews of Legal Frameworks: Policymakers should routinely update regulations to address the new, noisy gaps and tangled issues posed by advanced surveillance technologies.
- Public Engagement: Increasing dialogue with the public can lead to more informed decisions on what kind of surveillance technologies are acceptable—and what boundaries should not be crossed.
Industry and Government: Joining Forces for a Safer Future
It is clear that neither technological progress nor privacy protection can succeed in isolation. Finding your way through the maze of surveillance capabilities will require a collaborative approach. As industry leaders, technical experts, and government regulators put their heads together, we may be able to create systems that are both innovative and secure.
Concluding Thoughts: Balancing Promise with Prudence
Wireless tapping, as demonstrated through the combination of radar sensors and adapted AI speech recognition, stands at the intersection of opportunity and caution. It embodies the spirit of innovation, offering new possibilities in communication technology, security, and emergency response. However, it simultaneously exposes users to significant privacy risks if it falls into the wrong hands.
Key Takeaways from the Research
To summarize the key points discussed:
- The research establishes that remote listening through radar-detected vibrations is technically feasible, even if the results are only partially accurate.
- Using techniques like low-rank adaptation, researchers have adapted existing AI models to interpret noisy data—a process that, despite its promise, leaves room for error and incomplete understanding.
- The potential for both beneficial and malicious applications is large, demanding close attention from policymakers and industry stakeholders alike.
- Effective regulation, transparent research practices, and collaboration between public and private sectors are super important to prevent misuse while promoting technological growth.
Future Paths and Public Awareness
As we witness the evolution of such complex surveillance techniques, public awareness stands as a super important pillar in balancing innovation with privacy. Increased education and clear, transparent communication about the risks and benefits are necessary to ensure that society as a whole does not find itself in a situation where safety is traded off for convenience.
Call to Action for Stakeholders
The conversation surrounding this research should not be confined to academic journals alone. It must extend to community forums, legislative halls, and corporate boardrooms. Everyone, from technologists to everyday citizens, has a stake in determining how such capabilities should be integrated into the broader technological landscape.
Moving Forward: Integrating Technology with Caution
While the current wireless tapping experiments highlight how far we have come in terms of technical prowess, they also serve as a wake-up call. The ability to capture and partially decode conversations from vague vibrations is a double-edged sword. On one edge, it could lead to breakthrough applications in security and assistive technology; on the other, it potentially invades personal spaces in ways that could be deeply harmful.
Embracing a Culture of Responsible Innovation
To ensure that advancements in wireless tapping are used responsibly, a culture of responsible innovation must be embraced. This involves applying a cautious, measured approach that respects the rights of individuals while still harnessing the power of technological progress. It means recognizing and addressing the tiny details and subtle twists in the way data is captured, processed, and ultimately used.
Integrated Solutions for a Safer Digital Environment
Looking ahead, potential solutions to manage the risks include:
- Continuing to refine AI algorithms so that they can better handle noisy data environments.
- Developing integrated security frameworks that can monitor and block unauthorized access to sensitive signals.
- Investing in interdisciplinary research programs that combine insights from computer science, ethics, and legal studies to develop comprehensive privacy guidelines.
- Promoting public debates and educational campaigns to ensure that everyone is aware of both the benefits and the dangers inherent in these technologies.
Final Reflections: Technology, Trust, and the Way Forward
The work undertaken by researchers at Penn State offers a tantalizing glimpse into the future of communication and surveillance. As we figure a path through these new twists and turns, the role of policy makers and industry leaders is to ensure that technological innovations do not come at an overwhelming cost to personal privacy. It’s all about maintaining a balance where progress does not compromise the security of personal interactions.
By learning from this research, we as a society can better understand not only the potential applications of wireless tapping but also the critical need for ethical and responsible oversight. With robust oversight, transparent research practices, and strong public engagement, we can harness the benefits of advanced AI and radar technologies without risking our private conversations being decoded by unknown parties.
Ultimately, we must acknowledge that every new technological breakthrough carries with it a set of tricky parts and tangled issues that require careful thought and deliberate policy actions. The emerging field of wireless tapping is no exception. It challenges us to weigh the tangible benefits against the potentially intimidating risks. Now, as we stand on the cusp of this digital transformation, we have a unique opportunity to set the course for a future where innovation and personal privacy go hand in hand.
In Summary
The journey into wireless tapping—using radar sensors and adaptive AI—is a vivid example of how technological breakthroughs can simultaneously push the boundaries of what is possible and spark intense debates about privacy. Through methodical research and continual improvements in AI model adaptation, we have seen a path emerge that could revolutionize both security and communication if managed properly.
However, the quick pace of this innovation mandates that all stakeholders, including researchers, developers, lawmakers, and the public, stay engaged and vigilant. With informed public debates, clear ethical guidelines, and a proactive legal framework, we can hope to enjoy the benefits of this technology while keeping its potential pitfalls at bay.
As we move ahead, let every step be measured, every innovation be accompanied by a strong sense of responsibility, and every voice—especially that of the public—be heard. The delicate balance between embracing new capabilities and protecting the inherent rights of individuals will ultimately determine the future of digital communications in our modern, interconnected world.
Originally Post From https://www.psu.edu/news/engineering/story/conversations-remotely-detected-cell-phone-vibrations-researchers-report
Read more about this topic at
A Novel Radar Sensor for the Non-Contact Detection …
Conversations remotely detected from cell phone …